It seems like almost every week we see a new post by Matt Southern on a new WordPress site vulnerability or exploit. This is for good reason as WordPress accounts for over 23% of all of the websites on the internet, and that number is steadily growing.
Due to how many websites use the WordPress platform, it’s no wonder why hackers try to exploit this web platform constantly as they can potentially have access to a wide chunk of the internet if they succeed.
Don’t Think it Can’t Happen to You!
Like many WordPress site owners, I fell into the trap of not being more proactive about security on a few of my gently used personal sites. This came back to bite me with a vengeance this last December when I experienced the worst Christmas present any webmaster can receive – a big fat website hack!
The malware hack I experienced was especially nasty as it most likely exploited one of my websites through an older version of the Revolution Slider plugin that came with my theme. What I didn’t realize until months later was that this initial hack opened the backdoor to a widespread infection of other WordPress sites I had on my shared hosting solution. A four-month long nightmare then ensued which even resulted in me having to completely remake one of my websites on a completely new WordPress build and database.
So what’s the moral of the story? Unlike me, be more proactive about WordPress security.
Looking back at this whole experience, it’s clear that I made some pretty serious mistakes when it came to keeping my websites secure. Many of these mistakes could have been remedied by following some simple guidelines.
In order to help you avoid a potential security breach, here are 10 tips based on the things I have learned to help you keep your WordPress site more secure:
1. Verify Your Site with Webmaster Tools
As scary as it was to get an email from Google letting me know my site had been compromised, thank goodness they notified me! The last thing you want to have happen is to experience a website exploit and not even know about it.
By verifying your site with Webmaster Tools you can have access to important data that can be used to find a potential issue such as traffic, queries, and manual action messages. In fact, Google has an entire section in their Webmaster Tools panel dedicated to security issues to help you pinpoint where your website is experiencing problems.
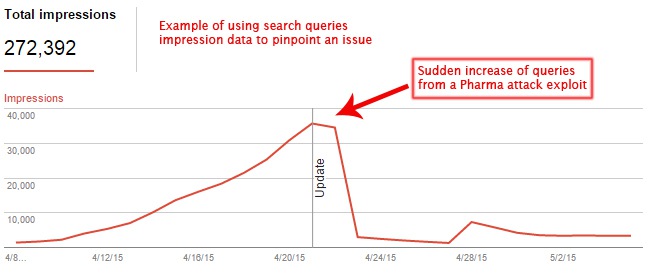
I personally have found the “Fetch as Google” functionality to be extremely helpful as you have the ability to see a page the way Google sees it. This is especially useful in the case of a pharma hack, which I experienced on one of my sites, in which the spam pages created by the hack are not visible to the normal user and only show up on Google’s crawler.
It’s also important to have your site verified as working with Google through their Webmaster Tools platform so you can request that your site be removed from the blacklist once a website hack has been resolved.
2. Update & Update Some More
Within the WordPress ecosystem, there are three components that need constant updating: WordPress itself, plugins, and themes.
WordPress Updates: One of the best things about WordPress is how quick they are to patch security holes and roll out updates. In fact, since WordPress 3.7, automatic security updates have been enabled on most sites. New version builds of WordPress however often need to be updated manually, and it’s important that you do so as WordPress constantly improves the platform with each release. If you aren’t sure how your updates are handled when WordPress makes a change, learn how to configure them here.
Plugin Updates: WordPress makes it very easy to see which plugins need to be updated by clicking on the “Plugins” tab on the admin dashboard. Some third-party plugins offer the option for auto updating, which I would absolutely recommend doing.
You can also force plugins to auto update by adding the following code to your wp-config.php file:
add_filter( ‘auto_update_plugin’, ‘__return_true’ );
Theme Updates: Themes are also susceptible to attacks, and a good theme developer will patch up and deploy an updated version whenever a vulnerability is found.
Many themes also have the ability to set up auto updating, but if not, here is an easy way to force automatic updates by changing your wp-config.php file:
add_filter( ‘auto_update_theme’, ‘__return_true’ );
3. Be Careful Who You Trust
One of the best things about WordPress is the staggering number of third party plugins that can be downloaded to add functionality and features to your website. Currently the WordPress Plugin Directory is counting 37,723+ plugins that you can install – that’s a butt load of plugins!
The sad reality is that whenever you layer something on top of an initial platform, it can create a whole new set of security holes and vulnerabilities. Most WordPress attacks often happen through vulnerabilities found in plugins and themes.
It’s also important to note that there are free plugins as well as premium plugins. Most people think that if they pay for a plugin that they are automatically safe from vulnerabilities. While having a paid development team definitely helps to thwart attacks, it doesn’t mean it’s a 100% guarantee that it will never happen. Even when a premium developer patches a known threat, you as the webmaster are still at risk until the plugin has been updated on your own website.

This was the case with my website and the Revolution Slider attack that compromised more than 100,000 websites at the end of last year. Due to my theme having been pre-packaged with the premium plugin, I was not notified that there was an update for the plugin due to me not having my own premium license (the theme developer most likely had a developer license to include the plugin in the theme which didn’t transfer to me as the user when I bought the theme). I was unable to update the plugin until after purchasing a license of my own, but by that time it was too late to prevent the damage that had already been done.
Since this attack, this plugin publisher has changed a few things to be more transparent, but be very wary of the plugins that come with themes and make sure you manually check to see if the developer of these plugins has pushed out an update that you would otherwise be unaware of.
Here are a few things to consider before installing a plugin on your website:
- Is the functionality of this plugin absolutely essential to provide the user with the best experience possible? If not, don’t install it.
- Has the plugin been updated recently? Every plugin on the WordPress Plugin Directory has a changelog (a list of changes and the dates those changes were made). If it hasn’t been updated in a long time, don’t install it.
- If it is a premium plugin, do they offer support and how are the ratings from other customers? Only choose plugins that have developer involvement and that are highly rated.
- Is there a plugin that can combine and consolidate features found in multiple plugins? Running fewer plugins helps to reduce the chances of an attack.
- Don’t ever install a free plugin from an unknown source…ever.
4. Scan Your Site Regularly
There are some pretty nifty tools out there that can scan your entire WordPress site for malware, added code, and other strange anomalies that may have been injected into your website.
Some of the most popular WordPress scanning plugins include: Wordfence, Sucuri Site Check and Code Guard to name a few. Many of these popular plugins also provide a free version which can be downloaded and used.
These scanners are an extremely valuable resource as they can help you to pinpoint files on your website that have been modified without your permission in order to find the harmful code that needs to be removed.
Most of these plugins can be configured to automatically scan your site in the background and send you a notification if it finds anything out of the ordinary.
5. Deny Multiple Login Attempts
Hackers often use what is called a “brute-force” attack which is a script that uses multiple random usernames and passwords to try to gain access to your website.
One of the best ways to stop this type of attack in its tracks is to block IP’s for multiple login attempts. Essentially this works by locking out a user from being able to access your site if they try to login to your WordPress admin a certain number of times.
This is almost always a feature included with the site scanning plugins listed above in section 4.
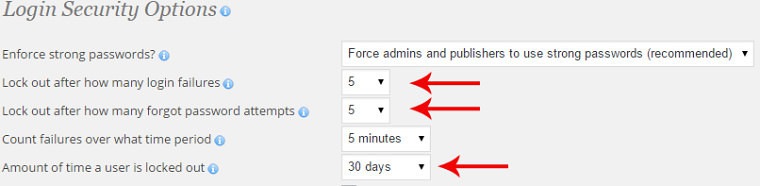
Once a user is locked out, the IP Address of the user will be recorded in a log so you can take extra measures to block those users indefinitely.
6. Database Security
In case you didn’t know, WordPress runs off of a MySQL database that was created on your web hosting server. This database has a username and password in order to set the data read and write privileges used by your WordPress build and some plugins.
This username and password should be strong and unique to that database only and should never be duplicated amongst other MySQL databases if you run multiple WordPress sites from the same server.
If you had someone else set up your website, verify that this is the case.
My mistake: Since my education at the school of hard knocks after my sites were compromised, I realized that I made a fatal error when it came to databases that I had created. Since I had a few WordPress sites that I had created for personal use on the same server, I gave all of the databases the same username and password so that I wouldn’t forget them. This was incredibly stupid as it meant that once one site was compromised, I made it that much easier for the attack to spread over into my other websites.
7. Never Use “Admin” as a Username
As to my point above about brute-force attacks, hackers use scripts trying to guess the username and password of your website in order to gain access. Up until WordPress 3.0, installing WordPress automatically generated the first user with the ‘admin’ username.
Since most WordPress websites have this user in their database, it is the most common username that these brute-force attack scripts use to try to gain access to your site. Chances are your website has the ‘admin’ username with administrative access, so let’s change that.
*Before doing any of these steps, make sure to back up your website. If you are uncomfortable making administrative changes, please consult a professional.
- In the users panel located on the main dashboard, click on ‘Add New User’ in the menu.
- Fill out the user information with a strong username and password and select ‘Administrator’ from the “Role” dropdown menu.
- Click on ‘Add New User’ once completing the form to create the new username.
- Log completely out of WordPress and log back in using the new user credentials.
- Go back to the user panel from the main dashboard and select the ‘admin’ username.
- Click ‘delete’ from the dropdown menu.
- Attribute all of the posts from the user ‘admin’ to the new username that you created when prompted.
8. Choose a Good Hosting Company
Nothing is more frustrating than to have a hosting company that provides next to nothing when it comes to support when dealing with a website attack – trust me, it sucks! It’s even worse to have to deal with an attack that is caused by your hosting company’s lack of security protection.
Since we live in a world where attacks are running rampant, make sure to choose a hosting solution for your WordPress sites that:
- Supports the latest versions of PHP, MySQL, CPanel, Plesk, etc.
- Supports and optimizes the running of WordPress
- Provides account isolation
- Has real people who you can talk to in case of an issue
- Has a robust backup solution
By following these tips, you will be able to ensure you have the right support and the tools necessary to avoid and recover from a potential WordPress attack.
9. Isolate Important Web Properties
Many of us run multiple WordPress installs off of one hosting account. While this isn’t inherently bad, it can create potential problems if one of your sites is attacked.
For example, in my situation, I had a shared hosting account with multiple websites running on the account. This not only increased my risk of all of my sites being vulnerable once one site was compromised, but it made restoring backups a total pain because most hosting services backup accounts, not individual websites. This means that to restore my infected website to a working version, I basically had to turn the clock back on my other uninfected sites.
Now I know there are ways around this, but the reality is that it takes a ton of time to manually download all your other sites via FTP and move them somewhere safe. When an attack happens, time is of the essence to get things back online, and wasting time moving non infected sites is a major hurdle.
So, if you have an important web property that receives tons of traffic or that is directly tied to your livelihood, at least isolate it with its own hosting account to make backup and recovery simple in the event something bad happens.
10. Have a Backup Plan
When it comes to WordPress, there are two things that have to be backed up in order to make your site work: website files and the database they are connected to.
I cannot stress enough how important it is to regularly backup your website in its entirety. Based on the seriousness of an attack and how crippling it is, a backup is sometimes the only way to get your website back to a semi-working state in order to start fixing the issues after an attack.
Most hosting accounts have a way to back up both your databases and your website files. There are even some WordPress plugins that can back up the database and website files of an individual WordPress site. Regardless of how you do it, the point is to back up your sites regularly.
Backups via your hosting company can typically be scheduled to happen daily, weekly, and monthly. Obviously the more the better, but remember that backups take up space, and depending on how much space you are paying for, you may be limited to the number of backups you can keep on your hosting account.
The other important factor to be aware of is that a backup on your hosting server is not 100% guaranteed. This means if the server that contains your websites goes kaput at your hosting company, those backups are subject to being lost. Because of this, it is a really good idea to have another backup stored somewhere else via FTP or on a local drive so that you are doubly covered from any potential data loss.
Conclusion
While it is impossible to 100% protect yourself from an attack, there are definitely things you can do to proactively combat the likelihood of one taking place on your WordPress site.
Having to deal with an attack is stressful, expensive, and in some cases can result in the loss of businesses and livelihoods.
WordPress security is serious, and with an average of 82,000 new malware threats per day, any time it takes to perform some of these tips is well worth it in the long run!
Are there any other big WordPress security tips you feel passionate about that you want to share? If so, I’d love to hear about it in the comments below.
Image Credits
Featured Image: Illustration by Greg Secrist
In-post Photo: Gajus/Shutterstock
All screenshots via Greg Secrist. Taken May 2015.




