WordFence researchers discovered a vulnerability in Elegant Themes Divi and Extra themes and the Divi Builder plugin. The vulnerability allows an attacker to completely take over a site.
The Divi Builder Plugin is a standalone plugin that allows a user to use the Divi builder functionality on any third party theme.
Elegant Themes Divi and Extra themes have the builder functionality built-in.
The vulnerability comes from a flaw discovered in the builder functionality in all three products.
What the Elegant Themes Vulnerability Is
The Elegant Themes exploit takes advantage of a vulnerability in a Divi feature that allows an a user with publishing or editing privileges to upload malicious files. An attacker first needs to compromise a registered user with those privilege levels in order to launch the attack.
The vulnerability affects the portability feature in Divi. This is a feature that allows a user with editor, contributor or author level credentials to import or export page templates.
It is this feature that lacks a specific check that allows a malicious attacker to upload PHP files that can then be used to take over an entire site.
WordFence Description of Vulnerability
WordFence offers a WordPress security plugin that protects against security issues. Their service includes testing WordPress plugins to find vulnerabilities.
Users of their premium plugin are protected against security issues as they are discovered.
WordFence describes how the vulnerability affects websites:
“This flaw made it possible for authenticated attackers to easily bypass the JavaScript client-side check and upload malicious PHP files to a targeted website. An attacker could easily use a malicious file uploaded via this method to completely take over a site.”
Elegant Themes Statement on Vulnerability
Although Elegant Themes’ announcement references “untrustworthy users,” this attack can happen to trustworthy users with a weak password or whose account is otherwise compromised.
Screenshot of Elegant Themes Changelog
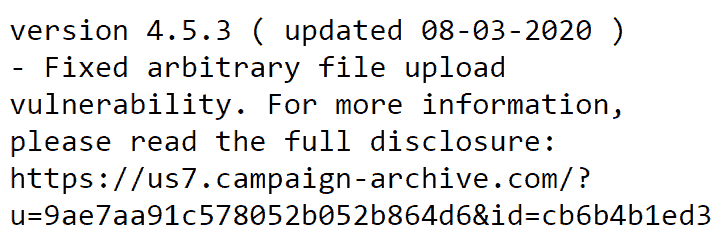 Screenshot of Elegant Themes’ changelog description of the vulnerability in Divi, Extra and Divi Builder WordPress plugin
Screenshot of Elegant Themes’ changelog description of the vulnerability in Divi, Extra and Divi Builder WordPress pluginAccording to Elegant Themes:
“Every website with potentially untrustworthy users that have access to the builder using Divi version 3.0 and above, Extra 2.0 and above or Divi Builder version 2.0 and above are affected and should update to the latest product versions.
Product versions 4.5.3 include the security patch.”
Security Patch Issued for Affected Elegant Themes Products
The vulnerability was discovered on July 23, 2020 by WordFence researchers. The security patch was tested and finally released on August 3, 2020.
Update Divi, Extra and Divi Builder Plugin
All publishers are encouraged to immediately update their Divi and Extra themes to version 4.5.3. Publishers with the standalone Divi Builder plugin should update that as well.
Citations
WordFence
Critical Vulnerability Exposes over 700,000 Sites Using Divi, Extra, and Divi Builder





![[SEO, PPC & Attribution] Unlocking The Power Of Offline Marketing In A Digital World](https://www.searchenginejournal.com/wp-content/uploads/2025/03/sidebar1x-534.png)