Google’s Chrome browser will begin warning users that non-HTTPS sites are “not secure” starting this week.
The exact date of the rollout is July 24, which is tomorrow at the time this writing.
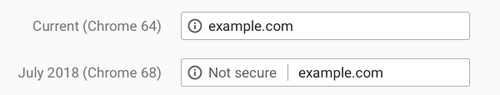
After that date, when a Chrome user lands on a HTTP site, there will be a warning in the address bar that the site is “Not Secure.”
Google has given site owners plenty of notice that this update was coming, dating back to February 2018.
In order to avoid the “Not secure” warning being displayed in Chrome, sites will have to migrate to HTTPS. Sites that have already migrated to HTTPS have nothing to worry about.
While this update will not prevent users from visiting non-HTTPS sites, it may cause users to think twice about which sites they visit.
The “Not secure” warning is part of Google’s push toward a safer web browsing experience. This is an ongoing effort that started back when Google made HTTPS a ranking factor in 2014.
HTTPS encrypts all information exchanged between a visitor and the website. That means it cannot be intercepted by hackers and other bad actors.
So when you submit confidential information via a web form, for example, you can be assured the information won’t fall into the wrong hands.
HTTP does not protect communications, so any information provided to a “not secure” website could potentially be stolen and used for malicious purposes.
Google Chrome is the second web browser to implement a warning for non-HTTPS sites, with Mozilla Firefox being the first.
Collectively, that accounts for 64% of all web browsing activity, according to StatCounter.
Microsoft Edge and Apple Safari currently do not show warnings for non-HTTPS sites.
For further information about HTTPS, please see the following resources:


