The publishers of the Ultimate Addons for Elementor plugin notified customers of a vulnerability affecting two of their plugins.
This is the entry in the changelog related to the patched Elementor Plugin that Brainstorm Force fixed in March 2021:
- Version 1.30.0 – Fixed – March 30, 2021
Hardened allowed options in the editor to enforce better security policies.
Brainstorm Force Elementor Plugin Vulnerabilities
The publishers of the Ultimate Addons for Elementor plugin notified customers of a vulnerability affecting two of their plugins.
The two affected plugins are addons for the popular Elementor page builder plugin. Addons are third party plugins that extend the functionality and features of the Elementor Page Builder plugin.
The addon plugins with vulnerabilities are published by a third party, Brainstorm Force.
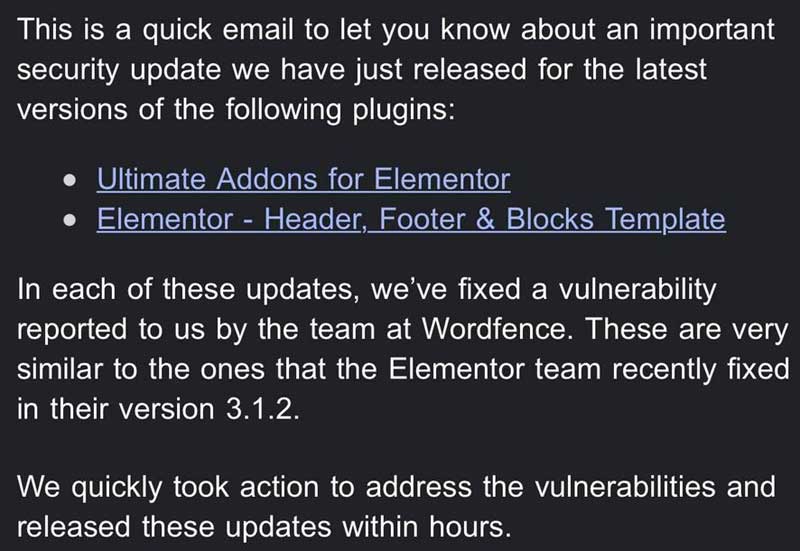
The affected plugins for Elementor are:
- Ultimate Addons for Elementor
- Elementor – Header, Footer & Blocks Template
An email sent by Brainstorm Force noted that they were notified of the vulnerabilities by the Wordfence security team and that they responded within hours.
According to the email:
“In each of these updates, we’ve fixed a vulnerability reported to use by the team at Wordfence.
These are very similar to the ones that the Elementor team recently fixed in their version 3.1.2.”
Screenshot of Brainstorm Force Email
The Elementor vulnerability that Brainstorm Force referenced is known as a Stored Cross-site Scripting Vulnerability, one that had the possibility of enabling malicious hackers to stage a full site takeover.
(Read: WordPress Elementor Vulnerability Affects +7 Million)
Stored Cross-site Scripting Vulnerability
Brainstorm Force did not explicitly say that the exploit patched was a Stored Cross-site Scripting Vulnerability. They only compared the fixed exploit to one that was patched by the Elementor page builder software.
A Stored Cross-Site Scripting Vulnerability is one in which a malicious script is uploaded directly to the website. This kind of vulnerability is generally considered to be more serious than another kind of cross site scripting (XSS) vulnerability called a Reflected XSS that depends on a link being clicked.
With a Stored XSS Vulnerability there is no need for a link to be clicked, the vulnerability exists on the affected website.
Wordfence Has Not Released Details
Wordfence has not released details of the vulnerability. As of this date, the only description of the vulnerability has been provided by Brainstorm Force as being similar to the Elementor page builder vulnerability.
But Brainstorm Force did not explicitly state that their plugin vulnerabilities are Stored XSS exploits. Only that they were similar to the Elementor vulnerability that was an XSS vulnerability.
Fixed Versions of Elementor Addons
The Elementor – Header, Footer & Blocks Template
The Elementor – Header, Footer & Blocks Template was patched on March 31, 2021 to version 1.5.8.
According to the changelog that documents what the updates contain, this update hardened it against a vulnerability.
This is what the changelog documented:
“1.5.8
Fix: Hardened allowed options in the editor to enforce better security policies.”
The fact that the editor needed hardening gives a clue that suggests that the vulnerability may be one that requires that a hacker have subscriber level privileges.
But this is not yet been officially confirmed at this time.
Ultimate Addons for Elementor
The Ultimate Addons for Elementor plugin was also patched on March 31, 2021 to version 1.30.0.
The reason given as to what was fixed is exactly the same as for the Elementor – Header, Footer & Blocks Template.
According to the Ultimate Addons for Elementor changelog:
“Hardened allowed options in the editor to enforce better security policies.”
Update Immediately
It is highly recommended that all publishers using these two plugins update their versions immediately.
The latest patched versions of the software are:
- The Elementor – Header, Footer & Blocks Template 1.5.8
- Ultimate Addons for Elementor 1.30.0





![AI Overviews: We Reverse-Engineered Them So You Don't Have To [+ What You Need To Do Next]](https://www.searchenginejournal.com/wp-content/uploads/2025/04/sidebar1x-455.png)