A flaw in a WordPress anti-spam plugin with over 200,000 installations allows rogue plugins to be installed on affected websites. Security researchers rated the vulnerability 9.8 out of 10, reflecting the high level of severity determined by security researchers.
Screenshot Of CleanTalk Vulnerability Severity Rating
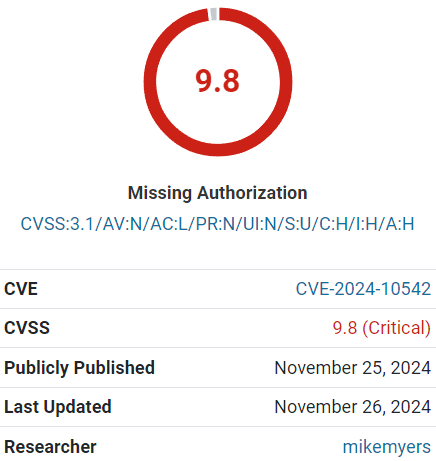
CleanTalk Anti-Spam WordPress Plugin Vulnerability
A highly rated anti-spam firewall with over 200,000 installations was found to have an authentication bypass vulnerability that enables attackers to gain full access to websites without providing a username or password. The flaw lets attackers upload and install any plugin, including malware, granting them full control of the site.
The flaw in the Spam protection, Anti-Spam, FireWall by CleanTalk plugin, was pinpointed by security researchers at Wordfence as caused by reverse DNS spoofing. DNS is the system that turns an IP address to a domain name. Reverse DNS spoofing is where an attacker manipulates the system to show that it’s coming from a different IP address or domain name. In this case the attackers can trick the Ant-Spam plugin that the malicious request is coming from the website itself and because that plugin doesn’t have a check for that the attackers gain unauthorized access.
This vulnerability is categorized as: Missing Authorization. The Common Weakness Enumeration (CWE) website defines that as:
“The product does not perform an authorization check when an actor attempts to access a resource or perform an action.”
Wordfence explains it like this:
“The Spam protection, Anti-Spam, FireWall by CleanTalk plugin for WordPress is vulnerable to unauthorized Arbitrary Plugin Installation due to an authorization bypass via reverse DNS spoofing on the checkWithoutToken function in all versions up to, and including, 6.43.2. This makes it possible for unauthenticated attackers to install and activate arbitrary plugins which can be leveraged to achieve remote code execution if another vulnerable plugin is installed and activated.”
Recommendation
Wordfence recommends users of the affected plugin to update to version 6.44 or higher.
Read the Wordfence advisory:
Featured Image by Shutterstock/SimpleB





![AI Overviews: We Reverse-Engineered Them So You Don't Have To [+ What You Need To Do Next]](https://www.searchenginejournal.com/wp-content/uploads/2025/04/sidebar1x-455.png)