WordPress.org and Wordfence have published warnings about hackers adding malicious code to plugins at the source, leading to widespread infections via updates, an attack that’s being referred to as a Supply Chain Attack.
Update 06-28-2024: More Plugins Are Infected
There have been more plugins identified as compromised:
- WP Server Health Stats (wp-server-stats): 1.7.6
- Ad Invalid Click Protector (AICP) (ad-invalid-click-protector): 1.2.9
- PowerPress Podcasting plugin by Blubrry (powerpress): 11.9.3 – 11.9.4
- Seo Optimized Images (seo-optimized-images): 2.1.2
- Pods – Custom Content Types and Fields (pods): 3.2.2
- Twenty20 Image Before-After (twenty20): 1.6.2, 1.6.3, 1.5.4
Read more: WordPress Plugin Supply Chain Attacks Escalate
Compromised Plugins: This Is What’s Going On
Typically what happens is that a plugin contains a weakness (a vulnerability) that allows an attacker to compromise individual sites that use that version of a plugin. But these compromises are different because the plugins themselves don’t contain a vulnerability. The attackers are directly injecting malicious code at directly at the source of the plugin, forcing an update which then spreads to all sites that use the plugin.
Wordfence first noticed one plugin that contained malicious code. When they uploaded the details to their database they then discovered four other plugins that were compromised with a similar kind of malicious code. Wordfence immediately notified WordPress about their findings.
Wordfence shared details of the affected plugins:
“Social Warfare 4.4.6.4 – 4.4.7.1
Patched Version: 4.4.7.3Blaze Widget 2.2.5 – 2.5.2
Patched Version: NoneWrapper Link Element 1.0.2 – 1.0.3
Patched Version: It appears that someone removed the malicious code, however, the latest version is tagged as 1.0.0 which is lower than the infected versions. This means it may be difficult to update to the latest version, so we recommend removing the plugin until a properly tagged version is released.Contact Form 7 Multi-Step Addon 1.0.4 – 1.0.5
Patched Version: NoneSimply Show Hooks 1.2.1
Patched Version None”
WordPress shut down all five plugins directly at the official plugin repository and published a notification at each of the plugin pages that they are closed and unavailable.
Screenshot Of A Delisted WordPress Plugin
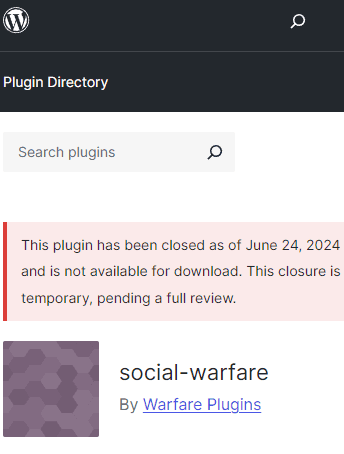
The infected plugins generate rogue admin accounts that phones home to a server. The attacked websites are altered with SEO spam links that are added to the footer. Sophisticated malware can be hard to catch because the hackers actively try to hide their code so that, for example, the code looks like a string of numbers, the malicious code is obfuscated. Wordfence noted that this specific malware was not sophisticated and was easy to identify and track.
Wordfence made an observation about this curious quality of the malware:
“The injected malicious code is not very sophisticated or heavily obfuscated and contains comments throughout making it easy to follow. The earliest injection appears to date back to June 21st, 2024, and the threat actor was still actively making updates to plugins as recently as 5 hours ago.”
WordPress Issues Advisory On Compromised Plugins
The WordPress advisory states that attackers are identifying plugin developers that have “committer access” (meaning that they can commit code to the plugin) and then in the next step they used credentials from other data breaches that match with those developers. The hackers use those credentials to directly access the plugin at the code level and inject their malicious code.
WordPress explained:
“On June 23 and 24, 2024, five WordPress.org user accounts were compromised by an attacker trying username and password combinations that had been previously compromised in data breaches on other websites. The attacker used access to these 5 accounts to issue malicious updates to 5 plugins those users had committer access to.
…The affected plugins have had security updates issued by the Plugins Team to protect user security.”
The fault of these compromises apparently lies with the plugin developer security practices. WordPress’ official announcement reminded plugin developers of best practices to use in order to prevent these kinds of compromises from happening.
How To Know If Your Site Is Compromised?
At this point in time there are only five plugins known to be compromised with this specific malicious code. Wordfence said that the hackers create admins with the user names of “Options” or “PluginAuth” so one way to double check if a site is compromised might be to look for any new admin accounts, especially ones with those user names.
Wordfence recommended that affected sites that use any of the five plugins to delete rogue administrator level user accounts and to run a malware scan with the Wordfence plugin and remove the malicious code.
Someone in the comments asked if they should be worried even if they don’t use any of the five plugins”
“Do you think we need to be worried about other plug-in updates? Or was this limited to these 5 plug-ins.”
Chloe Chamberland, the Threat Intelligence Lead at Wordfence responded:
“Hi Elizabeth, at this point it appears to be isolated to just those 5 plugins so I wouldn’t worry too much about other plugin updates. However, out of extra caution, I would recommend reviewing the change-sets of any plugin updates prior to updating them on any sites you run to make sure no malicious code is present.”
Two other commenters noted that they had at least one of the rogue admin accounts on sites that didn’t use any of the five known affected plugins. At this time it’s not known if any other plugins are affected.
Read latest development in the WordPress supply chain attack:
WordPress Plugin Supply Chain Attacks Escalate
Read Wordfence’s advisory and explanation of what is going on:
Supply Chain Attack on WordPress.org Plugins Leads to 5 Maliciously Compromised WordPress Plugins
Read the official WordPress.org announcement:
Keeping Your Plugin Committer Accounts Secure
Featured Image by Shutterstock/Algonga





![AI Overviews: We Reverse-Engineered Them So You Don't Have To [+ What You Need To Do Next]](https://www.searchenginejournal.com/wp-content/uploads/2025/04/sidebar1x-455.png)