When it comes to security, there is no WordPress-specific type of security that exists. All problems with security are common for all websites or applications.
WordPress security problems are of great interest, though, because it powers about 40% of the web and is open source. When one finds a vulnerability either in the WordPress core or plugins, other websites using it become vulnerable because they all use the same code.
On the other hand, there are a decent number of plugins that you can use to harden your website security.
In this column, you’ll learn how to harden your WordPress site against different types of vulnerabilities, though the scope of this article is wider and applies to all types of web applications.
Safeguarding Against WordPress Vulnerabilities
The most common types of vulnerabilities are:
- Backdoors.
- Pharma Hacks.
- Brute-force Login Attempts.
- Malicious Redirects.
- Cross-site Scripting (XSS).
- Denial of Service (DDoS).
These are the common types of vulnerabilities, but that doesn’t mean they are limited to just these. When you think about security, in general, you should think in a 360° way.
There is no limited set of ways to hack a website. Attackers can use many techniques to access your site.
For example, they can steal your PC and have physical access to your computer. They can also use surveillance techniques to see your passwords when logging in from a public network to your website.
Let’s dive into how to harden our WordPress installs in order to make life a little more difficult for attackers.
Keep reading to learn more about each of these 16 ways to harden your WordPress website security:
- Use HTTPS.
- Always use strong passwords.
- Use password managers to store your passwords.
- Enable Captcha on Login forms.
- Prevent brute-force login attempts.
- Use two-factor authentication.
- Keep up-to-date plugins.
- Set Security HTTP Headers.
- Set the correct file permissions for WordPress files.
- Disable file editing from WordPress.
- Disable all unnecessary features.
- Hide the WordPress version.
- Install a WordPress firewall.
- Keep backups.
- Use SFTP.
- Monitor users’ activities.
1. Secure Your Site With HTTPS
It isn’t by accident that we’ll start by securing the website with HTTPS.
Everything you do flows through the network and wire cables. HTTP exchanges data as plain text between browser and server. Therefore, anyone who has access to the network between the server and the browser is able to view your unencrypted data.
If you don’t protect your connection, you’re at risk of exposing sensitive data to attackers. With HTTPS, your data will be encrypted and attackers will not be able to read the data transmitted even if they have access to your network.
So the number one step for securing your website is enabling HTTPS. If you haven’t moved to HTTPS yet, you can use this guide to move your WordPress to HTTPS.
Tools & WordPress Plugins You Can Use to Migrate HTTP to HTTPS
2. Always Use Strong Passwords
The most common way hackers access websites is through weak or pwned passwords. These make you vulnerable to brute-force attacks.
Enhance your security by using strong passwords more than any other way listed below.
Always use strong passwords and check regularly if they have been pwned.
WordPress Plugins to Enhance Passwords Security:
3. Use Password Managers to Store Your Passwords
When you log in while working from a public network, you can’t be sure about who is watching what you are typing on your laptop or recording your passwords.
In order to solve this problem, use password managers to easily access your passwords and store them in a secure place.
Even if your PC is accessed, they will not be able to get your passwords. Password managers are browser-based and not WordPress plugins.
Password Manager Browser Add Ons:
4. Add CAPTCHA on the Login & Registration Form
When you’ve secured your website with HTTPS and used strong passwords, you’ve already made life for hackers pretty hard.
But you can make it even more difficult by adding CAPTCHA to login forms.
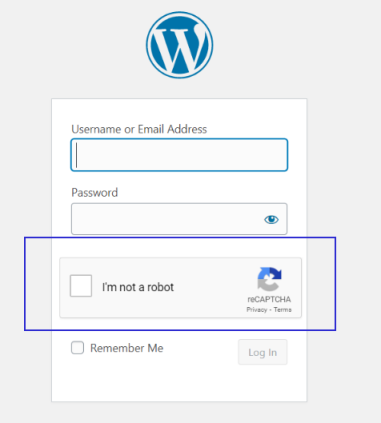
Captchas are a great way to protect your login forms against brute-force attacks.
Plugins to Add Captcha on WordPress Login:
5. Protect From Brute Force Login Attempts
Login CAPTCHA will give you protection against brute-force attempts up to a certain point, but not completely. Often, once captcha tokens are solved, they are valid for a few minutes.
Google reCaptcha, for example, is valid for 2 minutes. Attackers can use those two minutes to try brute-force login attempts to your login form during that time.
In order to solve this problem, you should block failed login attempts by IP address.
WordPress Plugins to Prevent Brute-Force Attacks:
6. Setup Two-Factor (2FA) Authentication
With secure passwords and captcha on login forms, you are more protected, yes.
But what if hackers used surveillance methods and recorded the password you typed on video to access your website?
If they have your password, only two-factor authentication can protect your website from attackers.
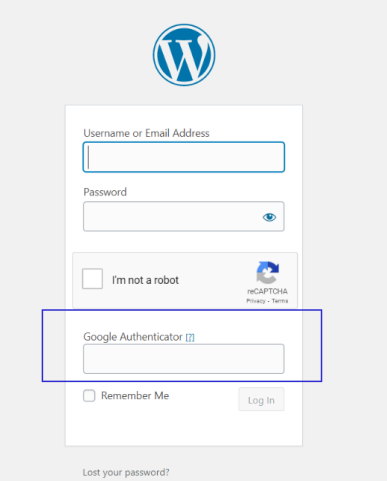
WordPress Plugins to Setup 2FA Authentication:
7. Keep WordPress Core and Plugins up to Date
Vulnerabilities occur often for WordPress core and plugins, and when they do they are found and reported. Make sure to update your plugins with the latest version in order to prevent websites from being hacked from known and reported holes in files.
I wouldn’t recommend switching to automatic updating since it could result in breaking your websites without your knowledge.
But I strongly recommend that you enable WordPress core’s minor updates by adding this line of code in wp-config.php since these updates include security patches for the core.
define( 'WP_AUTO_UPDATE_CORE', 'minor' );
8. Set Security HTTP Headers
Security headers bring an extra layer of protection by restricting the actions that can be performed between the browser and server when one browses website.
Security headers aim to protect against Clickjacking and Cross-site Scripting (XSS) attacks.
Security headers are:
- Strict-Transport-Security (HSTS).
- Content-Security-Policy.
- X-Frame-Options.
- X-Content-Type-Options.
- Fetch Metadata Headers.
- Referrer-Policy.
- Cache-Control.
- Clear-Site-Data.
- Feature-Policy.
We will not go deep into each security header explanation, but here are some plugins to fix them.
WordPress Plugins to Enable Security Headers:
9. Set Correct File Permissions for WordPress Files
File permissions are rules on the OS that host your WordPress files; these rules set how files can be read, edited, and executed. This measure of security is essential, especially when you host a website on shared hosting.
If set incorrectly, when one website on shared hosting gets hacked, attackers can access files on your website and read any content there – specifically wp-config.php – and gain complete access to your website.
- All files should be 644.
- All folders should be 775.
- wp-config.php should be 600.
The rules above mean your hosting user account can read and modify files and the webserver (WordPress) can modify, delete and read files and folders.
Other users can’t read the content of wp-config.php. If setting 600 for wp-config.php takes your website down, alter it to 640 or 644.
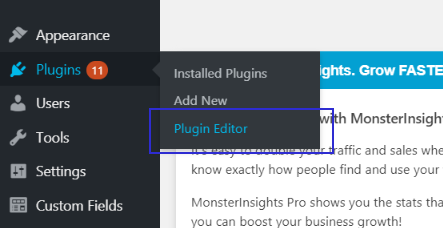
10. Disable File Editing From WordPress
It’s a known feature in WordPress that you can edit files from the admin backend.
It’s really not necessary because developers use SFTP and rarely use this.
11. Disable All Unnecessary Features
WordPress comes with many features you may not need at all. For example, the XML-RPC endpoint in WordPress was created for communicating with external applications. Attackers can use this endpoint for brute-force logins.
Disable XML-RPC using the plugin Disable XML-RPC-API.
Another issue that WordPress has built-in is providing a REST-API endpoint to list all users on the website.
If you append “/wp-json/wp/v2/users” to any WordPress install you’ll see a list of usernames and user IDs as JSON data.
Disable users REST-API by adding this line of code into functions.php
function disable_users_rest_json( $response, $user, $request ){
return '';
}add_filter( 'rest_prepare_user', 'disable_users_rest_json', 10, 3 );
12. Hide WordPress Version
WordPress automatically injects a comment with the version of WordPress in the HTML of the page. It gives the attacker the version of your installed WordPress as additional information.
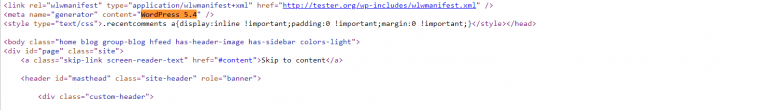
For example, if you are using a WordPress version whose core was reported to have a vulnerability, the attacker knows he can use the technique reported to hack your website.
Hide WordPress Version Meta Tags Using These Plugins:
13. Install a WordPress firewall
A firewall is a web application that runs on websites and analyzes any incoming HTTP requests. It applies sophisticated logic to filter out requests that potentially may be a threat.
One can set up its rules on top of the built-in rules of the firewall to block requests. One of the common types of attacks is SQL injection.
Say you run a WordPress plugin that is vulnerable to SQL injections and you don’t know about it. If you run a firewall, even if the attacker knows about the security flaw in the plugin, he will not be able to hack the website.
This is because the firewall will block those requests which contain SQL injections.
Firewalls will block those requests from the IP and prevent successive dangerous requests from coming. Firewalls are also able to prevent DDoS attacks by detecting too many requests from a single IP and blocking them.
It’s also possible to run DNS-level firewalls which run before requests are made to a web server. An example is Cloudflare DNS firewall.
The advantage of this method is that it’s more robust against DDoS attacks.
Application-level firewalls that run on the server let HTTP requests hit the webserver and then block it. That means the server spends some CPU/RAM resources to block them.
With DNS-level firewalls it doesn’t spend server resources, thus it’s more sustainable to attacks.
WordPress Firewall Plugins You Can Use:
- Wordfence Security.
- Sucuri.
- All In One WP Security & Firewall.
- BulletProof Security.
- Shield Security.
Note: If you decide to install firewalls, they may have features such as login brute-force protection or 2F authentication and you can use their features instead of installing the plugins mentioned above.
14. Keep Backups
If you get hacked, the best way to recover is by restoring the website from the latest version which wasn’t infected.
If you don’t store website backups, cleaning up the website may be a time-consuming operation. And in some cases, it may not be possible to restore all information because the malware erased all the data.
In order to avoid such scenarios, do regular backups of your website database and files.
Check with your hosting support whether they provide daily backups functionality and enable it. If not, you can use these plugins to run backups:
15. Use SFTP
A lot of developers already use SFTP to connect to web servers, but it’s important to make a reminder of this, just in case you still don’t.
Like HTTPS, SFTP uses encryption to transfer files over the network making it impossible to read as plain text even if one has access to the network.
16. Monitor Users’ Activity
We’ve discussed a lot of ways to secure your website from unknown hackers. But what about when one of your employees who has access to website admin does shady things such as adding links in content?
None of the above methods are able to detect a shady employee.
That can be done by watching activity logs. By looking into the activity of each user, you may find that one of the employees edited an article which they weren’t supposed to.
You can also look into activity that looks suspicious and see what changes were made.
WordPress Plugins to Monitor Users Activity:
Note that you may want to limit the period (or the number of records) these plugins keep. If there are too many, it will overload your database and may affect website performance and speed.
What to Do If You Get Hacked?
Even with all of the advice from security experts and knowing the ways to harden your websites from hacks, they still do happen.
If your website was hacked, you need to perform these steps below to recover:
- Change all of your email and other personal passwords first since hackers may have gotten access to your email first and thus be able to access your website.
- Restore your website to the latest known non-hacked backup.
- Reset passwords of all website users.
- Update all plugins if there are updates available.
Conclusion
Think 360° when it comes to security. Stress the importance of security to all of your employees so they understand the consequences the company may suffer if they don’t follow security rules.
If you get hacked, ]recover your website from the backup and change all passwords to your website and emails ASAP.





![AI Overviews: We Reverse-Engineered Them So You Don't Have To [+ What You Need To Do Next]](https://www.searchenginejournal.com/wp-content/uploads/2025/04/sidebar1x-455.png)