On November 20, 2018 Yoast released a security update to fix a vulnerability. This update was not announced on the Yoast blog. The vulnerability only affects users who have the SEO Manager role enabled. It does not affect all users of Yoast SEO.
Nevertheless, 77% of Yoast users have not upgraded to version 9.2 and may be unaware of the vulnerability.
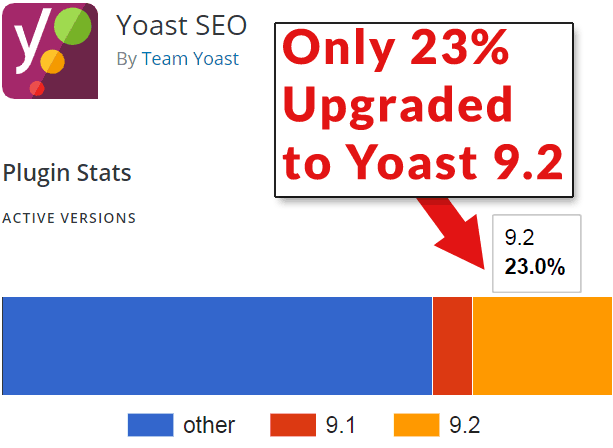 77% of Yoast Users are potentially vulnerable to the Yoast 9.1 hacking vulnerability. This is a screenshot of a graph from the official WordPress page of the Yoast SEO Plugin.
77% of Yoast Users are potentially vulnerable to the Yoast 9.1 hacking vulnerability. This is a screenshot of a graph from the official WordPress page of the Yoast SEO Plugin.This article seeks to help users by making them aware that the vulnerability exists and to responsibly encourage them to upgrade.
Nuance About the Yoast Vulnerability
A security expert discovered the vulnerability (called a Race Condition) and alerted Yoast and the security community. Yoast took immediate action and immediately fixed the vulnerability.
The vulnerability was a complicated issue called a race condition vulnerability.
It’s basically a situation where a software expects an operation to happen within a certain sequence. The vulnerability happens when that sequence is changed. This results in an opening where an attack can happen.
TechTarget defines a Race Condition like this:
“A race condition is an undesirable situation that occurs when a device or system attempts to perform two or more operations at the same time, but because of the nature of the device or system, the operations must be done in the proper sequence to be done correctly.”
How Does the Yoast Vulnerability Affect Websites?
The Yoast 9.1 vulnerability requires that a website have the Yoast SEO Manager role enabled. This is why this vulnerability does not affect all users.
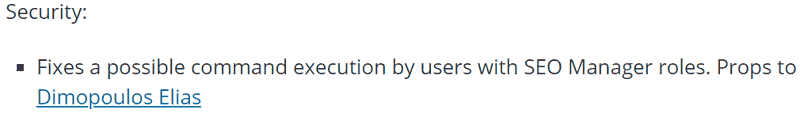
Which Versions of Yoast Does this Affect?
It is being reported that Yoast version 9.1 and under that have the SEO Manager role are affected. The security researcher who discovered the vulnerability said:
“I tested with Yoast 9.1 and 9.0.3.”
How Does the Yoast 9.1 Vulnerability Work?
I asked the security researcher how the vulnerability worked and he said that the attacker can target Yoast installations with the SEO Manager role enabled and then perform code execution exploits.
Here is what he said:
“The thing with the SEO Manager is that this role is not able to install plugin, themes etc on the WordPress, however the attacker can perform command execution.”
The goal of command execution is making undesirable changes to the website.
Does this Affect Sites without the SEO Manager Role Enabled?
I asked the security researcher if sites with the SEO Manager role not enabled were vulnerable. He advised that the possibility of being hacked because of this is remote if the role is not enabled. The possibility rises if the SEO Manager role is enabled.
“If you do not have SEO Manager and the zip archive can be uploaded only by a WordPress administrator, the impact is very low.”
Are Race Vulnerabilities Common?
I asked the security researcher if this is a preventable vulnerability. He answered:
“I would say that many developers are not aware of race condition issues.”
What if You Don’t Have SEO Manager Role Enabled?
In general, it’s a good practice to update to the latest version of your plugins. Security is never an issue until it’s an issue and web traffic has collapsed. Why become an object lesson to your competitors of what not to do?
If you are using a Yoast SEO 9.1 or earlier, it may be a good idea to update it. Keeping plugins updated is a security best practice.
More Resources
- Study Shows Web Security Directly Affects SEO
- SEO & Cybersecurity: How the SEO Industry Views the Relationship
- Yoast SEO Plugin 7.0 Bug Causes Ranking Drops
Images by Shutterstock, Modified by Author
Screenshots by Author, Modified by Author




![AI Overviews: We Reverse-Engineered Them So You Don't Have To [+ What You Need To Do Next]](https://www.searchenginejournal.com/wp-content/uploads/2025/04/sidebar1x-455.png)